16 Billion Reasons to Get Serious About Digital Identity
Passwords on Passwords on Passwords. Enough Already.
Sixteen billion sounds like a lot…because it is.
Over the weekend, CyberNews broke the story of the discovery of over 16 billion passwords scattered across over 30 datasets. The population of the Earth is 8.2 billion people, of which 5.6 billion have access to the internet as of February 2025. That works out to 2.8 passwords compromised per human on the planet that can access the internet. So, before we go any further, if you believe NONE of your passwords were compromised, let get something straight. You aren’t that lucky.
While people around the world change their passwords and cybersecurity experts give their perspectives on LinkedIn, we should be asking ourselves a really important question:
Why are we still doing this?
Specifically, why are we still using a system of passwords that malicious actors have decades of experience stealing and humans are notoriously bad at remembering and recording? There are still investigations to be conducted and analysis to be done, but a couple of things are clear:
The volume of passwords compromised suggests a systematic approach to stealing login credentials that is broadly known.
The volume also suggests that stealing login credentials is fairly simple.
Instead of asking ourselves why we aren’t using better password managers, perhaps we need to be asking ourselves why passwords are still the default method for access to systems and user authentication. Rather than continuing to collect more and more passwords, a 16 billion password breach should be the forcing function we need to move to a standardized digital identity. Digital identity solutions can at minimum reduce the attack surface that was exploited in this breach, but would deliver more security as well. But there’s a problem:
Digital identity efforts were stricken from the Biden Administration’s final cybersecurity executive order by the Trump Administration’s most recent cybersecurity EO. Digital identity has been a controversial topic in the emerging technology world and has had many starts and stops. The timing of this particular stop is frustrating. But most can agree that we need to do something different. These kinds of breaches cannot continue to be commonplace. In this post, we will look at the idea of identification and authentication before the internet and even before computers. This study is informative for understanding what digital identity is and why it is time to move toward this solution.
Who Are You?
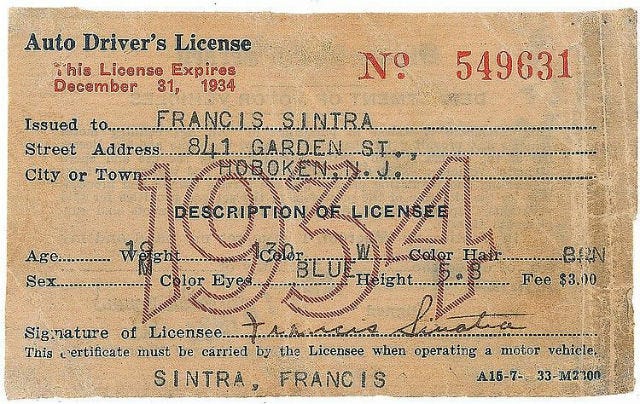
In the United States, the primary form of identification in the physical world is the driver’s license. The evolution of the driver’s license as a primary form of identification is curious because it was never intended to be used the way it is today. It began in 1889 when the mayor of Troy, New York started issuing licenses to operate horseless carriages up to six miles per hour on city streets. The story takes multiple twists and turns over the following 136 years, but where it started is important. Driver’s licenses were intended as a license to operate a piece of machinery and still function as such today. It was not until 1954 that the first state (South Dakota) required drivers to have licenses and in 1958, California was the first to put photographs on its licenses. Those photographs were not colored until 1972, but, again, that was just in California. My parents have memories of a simple paper driver’s license with no photograph at all. The simplicity with which a driver’s license could be faked would shock most people today.
States began standardizing photographs and making the licenses much more difficult to produce forgeries of, but there was still a problem.
The driver’s license relies on the person checking the ID to make a subjective match between the person holding it and the photograph. This is easily thwarted every year by thousands of teenagers that show an ID of someone that looks roughly like them to a bouncer at a dimly lit night club. There is no way to specifically verify that the person holding the ID is the person on the ID. There are two major questions when it comes to identification:
Is the ID card valid?
Is the person holding the ID card the person on the valid card?
Driver’s licenses were not designed to give this level of security and detail to those checking identification and there are consistently problems as a result. Driver’s licenses were meant to be licenses to operate machinery, not as national identification. Attempts have been made to improve this process, but the issues remain. In 2025, the federal government set standards for state issued identification cards through the REAL ID Act. This post-9/11 measure was intended to create more requirements for obtaining state ID cards such as proof of address. This helps prevent fraudulent cards from being issued but does not fix the questions above.
During the COVID-19 pandemic, the Commonwealth of Virginia issued electronic vaccine cards that came with a QR code. A checker could scan the QR code and see from the Virginia Department of Health that the holder had the vaccines on the card. That likewise does not validate that the person with the card is actually the person whose record is being queried.
This has significant parallels with how passwords are used in our cyber systems today.
The Password System
Passwords for our cyber systems are so common that we don’t often think about them. In many cases, they are somewhat of a burden. At some point, we realized that the number of individual accounts we had online, each with a unique password, was getting out of hand. The answer we came up with was not to perhaps reduce the number of passwords we have but to concentrate all of our passwords in a single password manager and use yet another password to protect them. When phrased this way, one can see the silliness of this approach.
Passwords rely on a shared secret. The shared secret is the password that is known by you and the service provider you are logging into. This requires BOTH of you to keep the secret. A compromise on either end results in a breach. Humans are notoriously bad at keeping this secret. People write them down, stick them under keyboards, and store them online. Companies also need to store the credentials somewhere, so the attack surface is huge. Sixteen billion passwords huge.
The core problems with the password system are as follows:
Centralized password databases (individual and service provider).
Password Reuse (same password for multiple services).
Weak Passwords
Phishing Vulnerability
All of these are well known and understood by most. Cyber hygiene helps mitigate these issues, but the core problems of the system remain. The shared secret model will always have inherent risks like using driver’s licenses for identification in the physical world.
Just as physical possession of a driver’s license does not authenticate the identity of the holder, possession of a password likewise does not authenticate the holder. This is the core of the problem with any password breach, let alone a massive breach of 16 billion passwords. We need to ask ourselves if the shared secret system is one we want to continue to stick with in light of the massive password breach. There is another option, but it has historically faced significant pushback and was recently removed from a federal executive order. Standardized digital identity.
Digital Identity
The idea of a standard digital identity is hardly new. The National Institute for Standards and Technology within the Department of Commerce published guidelines for digital identity in 2017. The idea behind digital identity is to create a digital system that authenticates who you are online, which currently does not exist. There are steps toward this such as the use of passkeys enabled with biometric requirements. Unlocking your phone with a fingerprint or facial recognition or using a fingerprint in place of a website password are examples. These are helpful and can reduce our requirement for passwords, but they still do not address the core problem. How can we verify that the person logging into the website is the person that owns the account? To achieve that, we need to explore different technical mechanisms:
1. Elimination or Significant Reduction of Stored Passwords
No Central Password Database Per Service: Instead of each service storing a user's password (or even a hashed version), a standard digital identity solution shifts the burden of authentication to a trusted Identity Provider (IdP).
Cryptographic Authentication (e.g., FIDO2/WebAuthn, PKI):
FIDO2/WebAuthn (Passkeys): This is a prime example of a standard in action.
Technical Benefit:
No Password Hash to Steal: There is no password or its hash for an attacker to steal from the service's database. Even if the public key database is compromised, it cannot be used to log in, as the private key remains on the user's device.
Phishing Resistant: Since the authentication relies on a cryptographic challenge tied to the domain, phishing sites cannot trick the authenticator into revealing the private key or signing a challenge for the wrong domain.
2. Federated Identity and Single Sign-On (SSO)
Delegated Authentication: Users authenticate once with a trusted IdP (e.g., Google, Microsoft Entra ID, Okta, or a government-backed digital ID system).
Security Assertion Markup Language (SAML) / OpenID Connect (OIDC): These open standards enable the IdP to securely communicate authentication and authorization assertions to multiple RPs.
Technical Benefit:
Reduced Attack Surface: Only the IdP needs to manage the primary credentials. Services no longer need to maintain separate password databases, significantly reducing the number of targets for attackers.
Eliminates Password Reuse: Since users authenticate through a single IdP, there's no incentive or need to reuse passwords across individual services.
3. Enhanced Multi-Factor Authentication (MFA) by Default
Integrated Strong MFA: A standard digital identity solution would intrinsically encourage and often mandate stronger MFA methods than traditional SMS or basic authenticator app codes. This could include:
Technical Benefit:
Even if an attacker somehow compromises a part of the authentication flow, the mandatory second factor, especially phishing-resistant ones, makes account takeover exceptionally difficult.
Whether or not digital identity can be done is not the question. The question is whether we as an internet using society are ready for the shift. Historically, the answer has been that we are not. When faced with growing numbers of passwords, our response was to centralize them and protect them with one password. Digital identity has faced significant pushback from critics who draw parallels with China’s Social Credit system while other decry it as government overreach. With 16 billion passwords compromised, we know for sure that the password model is ineffective and dangerous. That volume suggests that stealing passwords is hardly sport at this point and just something that’s done mechanically by malicious actors around the world. Do we really think we can figure out how to make a password manager that really will protect us this time? Or should we be thinking about new technologies?
Digital identity solves a problem that has vexed identification since the idea of identification was born. Connecting the physical person with the identification remains difficult with physical cards and is equally difficult with online accounts. From these two facts springs all manner of fraud, theft, and pain for those whose identities, passwords, and credentials are stolen. Instead of accepting this world and trying to enforce password rules, it may finally be time to get serious about digital identity. If you are looking for a reason to at least explore the option, I can give you 16 billion of them.
Connect with us: Substack, LinkedIn, Bluesky, X, Website
To learn more about the AI products we offer, please visit our product page.
Nick Reese is the cofounder and COO of Frontier Foundry and an adjunct professor of emerging technology at NYU. He is a veteran and a former US government policymaker on cyber and technology issues. Visit his LinkedIn here.